Quick overview of a physical unclonable function
At the heart of security systems lie secret keys as indispensable elements. Especially in hardware solutions, private keys are often stored in Hardware Trust Anchor (HTA). While this is deemed an acceptable approach, it carries a substantial manufacturing expense. Therefore, securing and managing secret keys emerge as challenging problems in hardware security, so manufacturers find themselves in need of a solution that offers a trifecta —low cost, high security and supply chain simplicity —for their physical devices. Hence, a physical unclonable function is proposed.
PUF, a concept that has been around for a considerable amount of time, has a physical structure that is easy to fabricate but impossible to replicate from the manufacturing deviation point of view. This inherent property makes it suitable for various cryptographic functionalities, such as fingerprinting for devices and generating private keys to be used in verification.
Theoretical basis
Physical unclonable function is based on the Challenge Response Authentication Mechanism (CRAM), which is the most common method of authentication. More precisely, when it receives a challenge, c, a related response, r, is returned.
To determine if a physical unclonable function is good or not, the two following metrics are defined.
- Inter-distance: For any particular challenge, this is the distance between two responses that are returned from two different PUFs
- Intra-distance: For any particular challenge and a PUF, this is the distance between two responses that are returned from two evaluations
An ideal PUF should have an inter-distance of around 50%, while its intra-distance should be near 0%. However, the intra-distance of PUF usually exceeds 0% as one single challenge often corresponds to multiple responses. To be recognized as a usable PUF, the distance among responses should be small. From a theoretical perspective, ‘small’ is dependent on the distance being chosen. There are unlimited existing distance metrics that can be used, such as Hamming distance, Euclidean distance and self-defined distance.
Taxonomy
Based on the security level and the exact number of unique challenges the PUF can process, PUFs are divided into two types [1]:
- Strong PUFs: Can support a large enough number of challenges, such as complete determination/measurement of all challenge-response pairs
- Weak PUFs: Can only support small challenges (in some cases, only a single challenge)
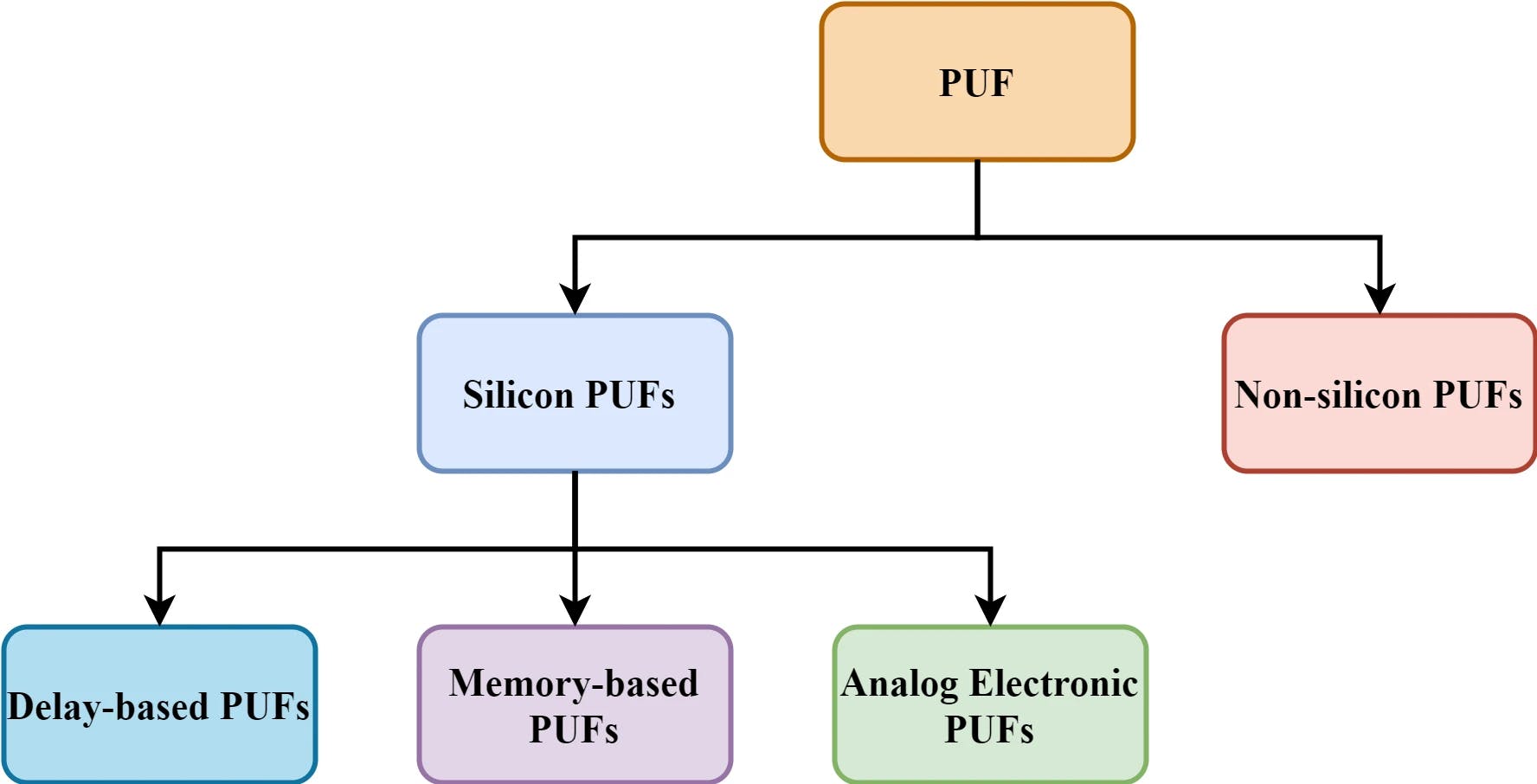
On the other hand, if a PUF is related to electronics, it can be categorized into the following:
- Silicon PUFs: These play a crucial role in identifying discrepancies caused by the manufacturing process variations of the integrated circuits (ICs). Inside silicon PUFs, there are 3 sub-categories: Delay-based PUF, Memory-based PUF and Analog/mixed-signal PUF.
- Non-silicon PUFs rely on the difference between objects by the operator that are not electronic. Accepted PUFs of this type include O-PUF (Optical PUF), P-PUF (Paper PUF), CD-PUF (Compact Disc PUF) and RF-ADN (Radio Frequency PUF).
PUF technology for security
In the current day and age, PUF technology has gained significant recognition as potential cybersecurity solutions for embedded systems and Internet of Things (IoT) devices [2]. With the expansion of IoT, the need to secure these devices has reached an unprecedented level. In an unforeseen circumstance, if a multitude of IoT devices are hacked, computer criminals can create DDoS attacks on the server or provide contaminated training datasets for big data systems. Integrating PUF with IC leads to the enhancement of its security in key generation, storage and usage process.
Following are a few PUF technology-based use cases that are implemented in hardware security:
- Using PUF-based security as a Hardware Root of Trust. Moreover, by supporting some cryptographic primitives, the Hardware Root of Trust can be extended to be Hardware Trust Anchor
- PUF-based security can be combined with a true random number generator (TRNG) for increasing the security of the semiconductor supply chain and anti-counterfeit operations
- Used for building Crypto Coprocessors that support key generation, key storage and computing with a secure cryptographic algorithm
Until now, most state-of-the-art PUF-based security solutions have been proposed in the semiconductor domain.
However, based on the promising capabilities of PUF technology, researchers and organizations have started to explore its application in other domains. Take the battery industry as an example, where applying PUF has taken on significant importance. PUF is being employed to effectively manage and verify battery lifecycle, state of health and other telemetries. A majority of PUF-based projects in the battery industry achieve lower than TRL4 on 9 levels of the Technology Readiness Level Management System. So, there is a lot of work to make those ideals become products.
Below are numerous directions that need to be addressed with PUF. These problems spread from a theoretical basis to the implementation aspect:
- Controlling PUF's quality impact factor: PUF is dependent on many components that interact with each other. Each component can impact the others, which in turn leads to a distinctly different response (i.e., domino effect). Hence, we need to minimize the number of components in PUF for performance optimization.
- Handling false positivity and negativity: Multiple responses can relate to a single challenge. If a distance is not well designed, it can lead to a high number of false positives or false negatives. Therefore, finding a suitable distance becomes a critical task for the application of PUF in different domains.
- Optimizing manufacturing processes: An example is when using PUF as the fingerprint for physical devices. Each device needs to join an enrollment process before the release and verification process in actual use. Improving these processes can reduce operational expenditure.
- Broaden PUF applications: PUF can be integrated with physical devices in other domains. These include insurance, banking, eCommerce, battery, telecommunication, healthcare and anti-counterfeit.
Conclusion
We delved into the physical unclonable function realm, exploring its theoretical basis and advanced concepts. The application of PUF can be extended to various industries such as battery, anti-counterfeit and others. Despite multiple challenges with PUF that need to be resolved, by embracing a good vision and strategy, PUF can turn out to be a promising business proposition worth examining.
References:
- McGrath, Thomas, et al. "A puf taxonomy." Applied Physics Reviews 6.1 (2019): 011303.
- Shamsoshoara, Alireza, et al. "A survey on physical unclonable function (PUF)-based security solutions for Internet of Things." Computer Networks 183 (2020): 107593.


