The current environment is changing the norm for operations, and we are anticipating a shift in the industry toward the next generation’s way of adopting technologies. Manufacturers must pivot their capabilities and the way they design, develop, deploy and test to start supporting remote efforts. These new capabilities may mean more automation on factory floors or the introduction of smart systems that will reduce human intervention.
Control systems in operational technology (OT) are essential to critical infrastructure for any industry. Traditionally, the employees, OEMs and manufacturing vendors perform maintenance activities in person on OT assets, which are repeated periodically. The digital transformation journey now has those activities being performed remotely. This requires that users be granted privileged access for a limited time, because if this access is unmanaged and unsupervised in a secure remote access or endpoint security system, it can lead to significant cybersecurity risks. In this blog post, we examine an approach to building a secure solution in an OT environment by leveraging the best-of-breed technologies and smart endpoint security management concepts.
As-is scenario
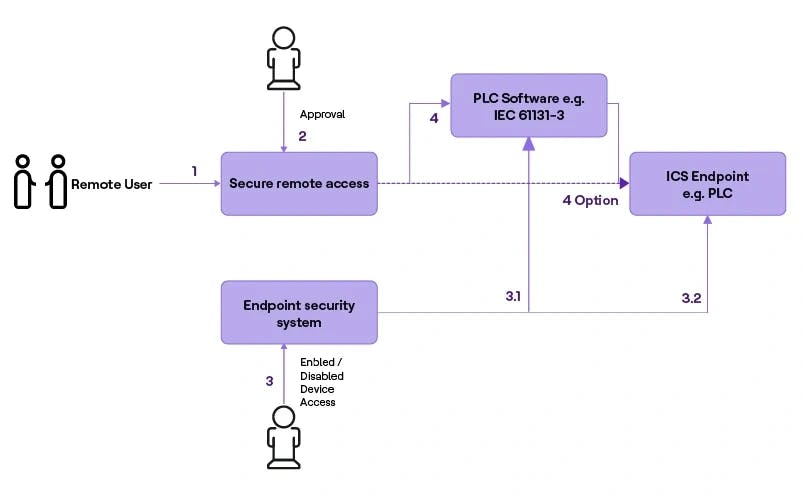
Figure 1 – “As-is for secure remote access”
Figure 1 shows the as-is scenario for secure remote access in an industry environment. There must be a user with administrator privileges who can approve the remote user request in the secure remote system and provide the access manually in the endpoint security system. Components utilized include:
Industrial Control System (ICS)
Programmable Logic Controller (PLC) acts as an endpoint and PLC software is written in high-level programming languages to program the PLC.
Secure remote access
Provides real-time visibility over OT assets. The admin user manually enables access to ICS for maintenance and upgrades. It does not have insights about the health and protection of the endpoint device.
Endpoint security
This is the practice of securing endpoints of end-user devices, such as desktops, laptops, PLC and mobile devices, from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network from cybersecurity threats. The person has to initiate the approval in a secure remote access system (2) and endpoint system (3) separately.
Challenges
Day-in-the-life scenario: The operational team has the following challenges:
- System functions independently in silos
- The remote user is granted access from the remote access system but is unable to perform the required activities until the endpoint system enables access. This leads to unnecessary delays in maintenance activities.
- Secure remote access will close the connection once the user completes the activity, but the ICS endpoint system is not protected immediately and left open, which leads to a security threat to the ICS network.
- Manual process to manage access
- Enable and disable remote user access to the ICS endpoint system.
- Identify and manage the ICS endpoint.
- Expertise is required to help each remote session's activities.
Operational smart approach
The Operational smart approach eliminates manual intervention and enhances the security of the ICS endpoint.
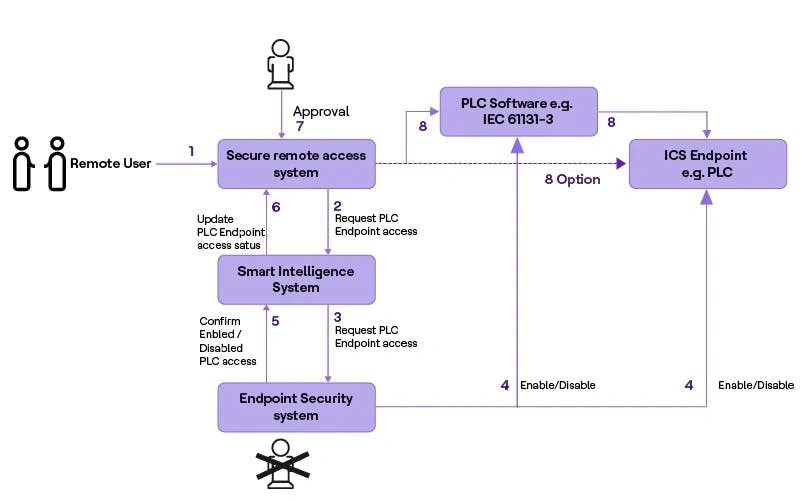
Figure 2 – “Operational smart approach”
An approach to effectively manage the endpoint security and secure remote access system is described in Figure 2. The remote access system can be integrated with the endpoint security system using standard communication. If the remote user wants to perform maintenance activities on the PLC, the user can raise a request with a justification in the secure remote access system. Using the Smart Intelligence System, it will process the remote user request with the endpoint security system automatically to provide access to the relevant PLC end device for a predefined duration. Once the endpoint is enabled by the endpoint security system, the system confirms the endpoint to the secure remote access system. The secure remote system can then approve the remote user request to perform the activity on the PLC end device.
Once the remote user completes the activity, the system automatically requests the endpoint security system to disable the access to the relevant PLC end device immediately. With the smart approach, the system can provide access in the endpoint security system immediately or during any requested time period in the future. This approach can be further enhanced by combining an IT service management ticketing system in the factory environment, for example, ServiceNow, to further automate and eliminate the need for the manual intervention and reinforce automatic remote user request access approval (7) based on the ticket status verification. The system should also be capable of sending email alerts when any abnormalities, threats or breaches occur in the system.
Benefits
- Increase productivity by reducing ICS endpoint attack surface
- Improve remote access governance
- Save resource cost by reducing resource involvement in managing ICS endpoint
- Secure endpoint by controlling endpoint security effectively
- Ensure effective business continuity by securely enabling remote work
The Operational smart approach is necessary to standardize and eliminate the need for manual intervention. This improves the endpoint security in an industry environment, where it is required to manage more remote users, such as third-party technicians, vendors and employees who need frequent access — especially given the pandemic situation. Eventually, this approach will converge with other solutions in the new IoT and OT security ecosystem.




