Overview
A contact center is at the center of a customer experience. Contact Center frauds are becoming increasingly common, and cyber criminals are targeting contact centers to gain access to sensitive customer information by exploiting agents and weak authentication processes.
Fraudsters can damage a brand's reputation, resulting in compliance liability, especially in heavily regulated industries like healthcare and financial services. Therefore, it becomes quintessential for business leaders to implement robust security measures to protect consumers and contact center operations.
Why do contact centers need a fraud detection and prevention mechanism now?
A contact center support agent manages sensitive data. They are crucial in the value chain as they sit between fraudsters and sensitive customer information. Hence, they naturally become favored targets by cybercriminals. Fraudsters are using advanced attack mechanisms to exploit vulnerabilities in customer service operations. According to research by Genesys, every 1 in 500 calls that come to a contact center is done by a fraudster. This is expected to increase multi-fold in the coming years. Fraudsters are attempting to infiltrate using withheld numbers (a number that the caller ID mechanism cannot identify), spoofing customer numbers, or simply moving too quickly for traditional rule-based controls to detect.
While there are many types of fraud happening in contact centers, the most detrimental among them are:-
- Identity theft: According to data from the US Federal Trade Commission (FTC), there were more than 1 million complaints of identity theft in 2023 in the US, which resulted in related losses exceeding $10 Bn.
- Account takeover: According to Ping Identity, account takeover frauds have surged by 354% in 2023. ATO Frauds resulted in nearly $13 Bn in losses in 2023.
- Card Not Present Scams (CNP): According to Emarketer, CNP Fraud accounted for $9.49 billion in 2023, making up 73% of card payment fraud.
There is a need to develop a connected security fabric around your contact center infrastructure
Comprehensive agent training, authentication processes and techniques and advanced fraud detection solutions are necessary to mitigate the chances of fraud.
Businesses should take a step-wise approach to achieving the goal. The approach should consist of:
Step 1 | Undertake a comprehensive security framework audit
The need of the hour is for contact center leaders to have a comprehensive assessment of existing security frameworks within their organization. An ideal security framework audit should include the following:
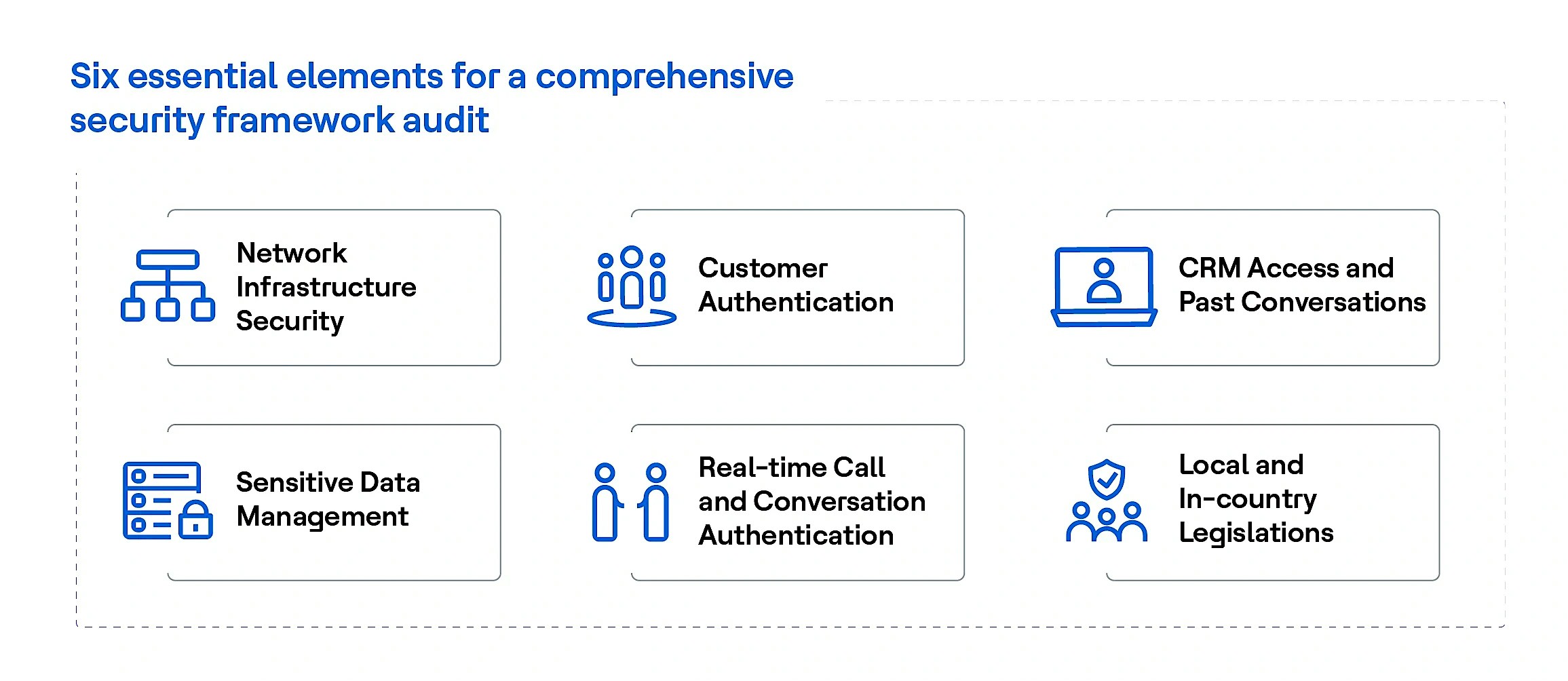
Six essential elements for a comprehensive security framework audit
Step 2 | Design, architect and implement a custom-designed fraud detection fabric
As contact centers transform from multichannel to omnichannel to dynamic channels, they need to adopt a layered, cross-channel strategy. Fraudsters can bypass security checks using sophisticated techniques like voice modulation and impersonation.
This calls for a holistic security posture to protect your contact center. The way it can be achieved is to have a connected and structured process of fraud detection along with different fraud detection tools that play a crucial role. Key solutions that should form part of the fraud detection strategy should include:-
- Identity verification: Fraud detection technologies that use a mix of possession information with reputation and ownership score. Pairing it with biometric authentication can enhance further.
- Multilayer authentication: Identity and access management solutions like 2FA, one-time password or OTP. Pair it with advanced technologies to track the origins of calls based on flagged IP addresses, etc.
- Voice biometrics and facial recognition: Voice biometrics solutions can detect anomalies in speech patterns, response speeds or changes in accent and tone. Facial recognition can further strengthen the process.
- Real-time customer interaction analytics: Real-time customer interaction analytics solutions and AI-based advanced techniques monitor suspicious behavior, such as rapid account changes, unusual transaction patterns or deviations in customer information. Pooling them with account takeover protection solutions can add to the security posture.
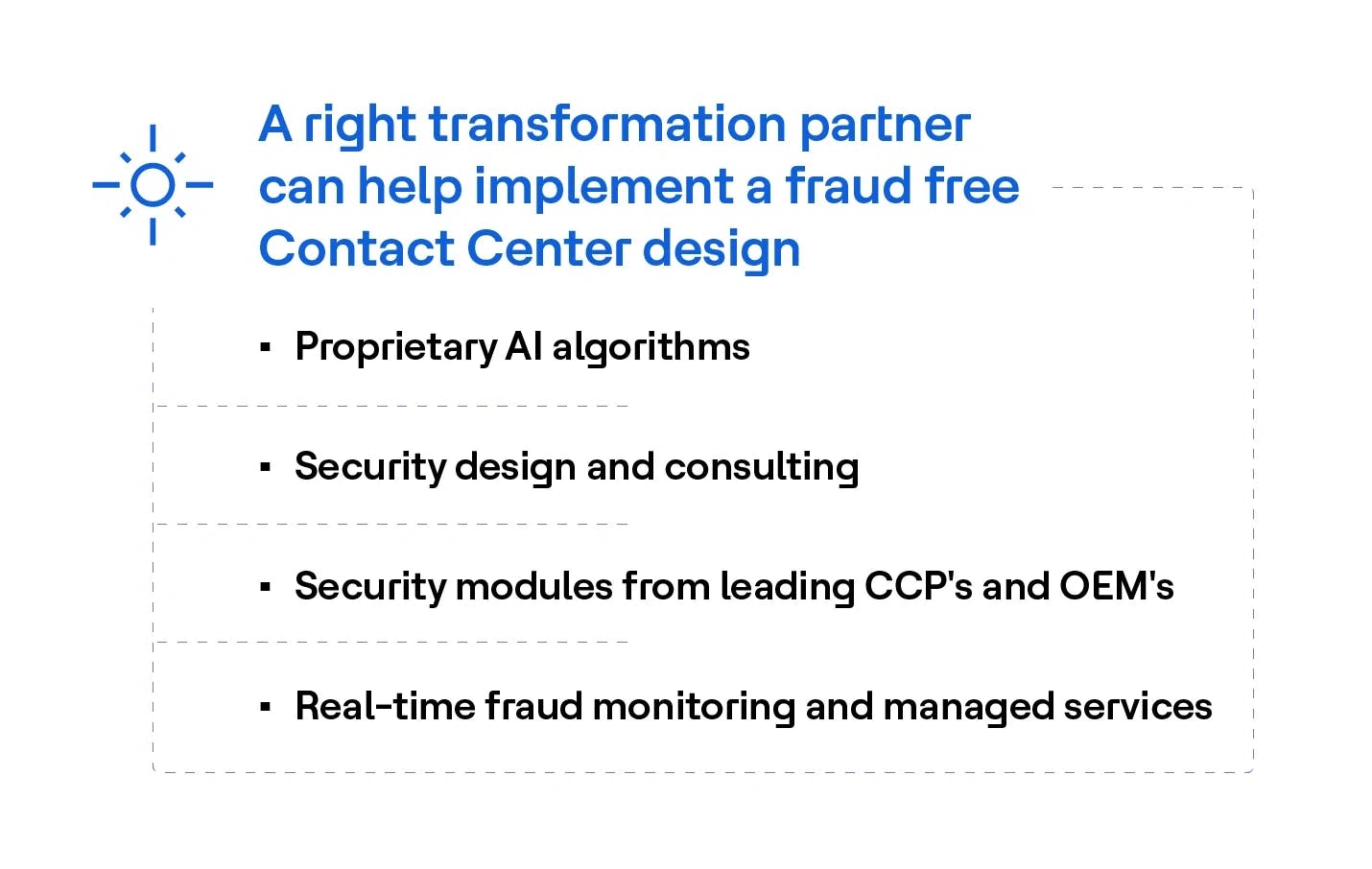
The right transformation partner can help implement a future-proof, fraud-free contact center design that adapts to evolving threats and regulatory landscapes, safeguarding business for the long term
To learn about our AI-powered contact center solutions, visit: LINK
Get insights into how our Fluid Contact Center Solution provides a value-driven CCaaS transformation at LINK



