The rapid advancement and adoption of technology have elevated industrial operations in the manufacturing industry in recent years. The complex mix of Information Technology (IT), Operational Technology (OT) and connected technologies ensures seamless operations and intelligent manufacturing. However, with the rise in cyberattacks, securing IT/OT convergence and protection against cyber threats require specialized solutions. These solutions should be designed and implemented with advanced security controls such as unified visibility of all assets, detection of anomalies and threats and comprehensive security measures for protection against cyber breaches.
Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) have been the backbone of the manufacturing industry for a long time, trusted by most organizations to ensure high productivity, cost-effectiveness and smooth operations. The adoption of Industry 4.0 and newer strategies leverages existing ICS and SCADA environments, coupled with connected OT devices that have proliferated the environment recently. These additions in technologies have introduced added risks and changed the dynamics of managing cybersecurity in ICS.
Market trends and forecast of Security of Things (SoT) in manufacturing
- As per the Harvard Business Review, the average cost of a data breach reached a record high of $4.35M in 2022
- The "State of IoT—Spring 2023" report states that global IoT connections grew by 18% in 2022 to 14.3B active IoT endpoints
- Juniper predicts 83B connected IoT devices globally by 2024, with 70% in the industrial sector
- MarketsandMarkets estimates that the operational technology security market is valued at $15.5B and will maintain a compound annual growth rate of 15.8% from 2022 to 2027, reaching $32.4B
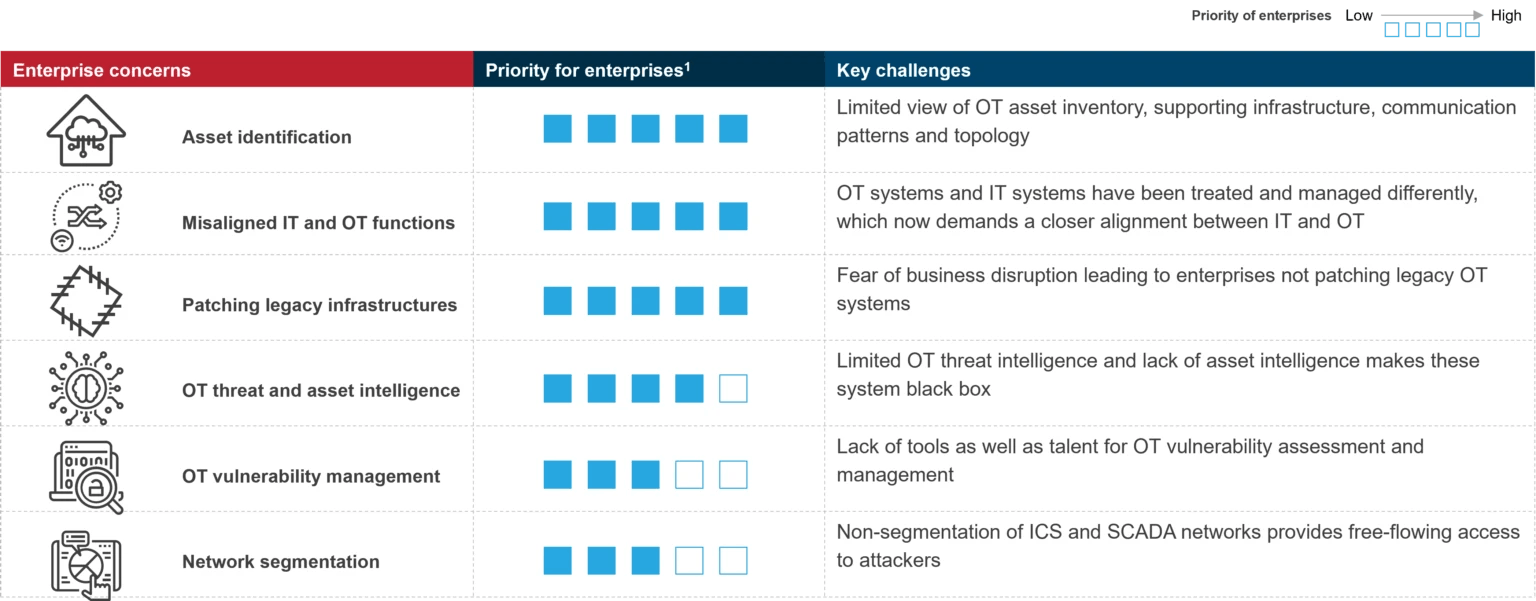
Challenges of OT Devices:
The adoption of OT devices is essential, and most manufacturing organizations are implementing Industrial Internet of Things (IIOT) devices to manage connected assets, facilities and infrastructure to improve efficiency. However, these advanced technologies open doors for cybercriminals and create new challenges:
- Increase in vulnerabilities and malware infection: OT devices are not as secure as they should be. Most devices are not built on the fundamental “secure by design” principle.
- Software updates and patching are cumbersome: Patching is more difficult and expensive for OT devices, leading to frequent cyberattacks and making devices vulnerable to threats and anomalies.
- IT and OT are fundamentally different: IT and OT use different languages, and their methods to secure and control manufacturing and industrial systems are entirely different.
Securing OT devices with HCLTech's OT security solution
Tracking IT and OT devices in manufacturing organizations is a complex process. It requires a deep understanding of the network, connectivity, technology and proper control and visibility of the OT and IT landscapes. At HCLTech, we’ve leveraged 25 years of global, cross-industry experience to create a solution that addresses the four critical dimensions of any industry: assets, people, technology and process/compliance.
HCLTech's 360° SecureOT is precisely that solution since it is designed to address the dynamic, complex and evolving nature of OT/IIoT cybersecurity requirements. It offers in-depth visibility, enabling real-time passive and autonomous monitoring of all connected systems and data flow. This robust security architecture is designed to help organizations adhere to industry standards and regulatory compliances such as ISA/IEC 62443, NIST and NERC CIP. Moreover, the program is backed by a seasoned team of cybersecurity architects and technical experts with core OT experience, available globally and across industry verticals.
With HCLTech’s 360° SecureOT advantage, enterprises can extend their security with next-generation threat intelligence and intel capabilities. We have managed OT Security Services (MSSP) for global customers with large and complex organizational structures to simplify their visibility and access challenges to get ahead of the latest threat vectors in industrial environments.
HCLTech's 360° SecureOT platform assists manufacturing organizations by:
- Providing complete visibility of assets in IT and OT networks with real-time monitoring to verify equipment operation
- Offering near real-time detection of threats and alerts and management in case of unusual activity
- Enabling proactive risk management through continuous monitoring
- Facilitating threat containment and remediation in case of a cyberattack or ransomware attack
- Implementing network segmentation to protect your critical infrastructure using network zones and segmentation
- Controlling any third-party access to your network and limiting specific access according to need and use
- Assessing your current compliance with critical components of regulatory frameworks and addressing gaps to protect your facilities.
Conclusion
While keeping pace with the adoption of niche technologies is crucial, securing the environment from cybercriminals is equally essential. OT aids manufacturing firms in increasing automation, improving people and processes and managing seamless operations across various departments within the organization. However, OT exposes security vulnerabilities and acts as an entry point for cyberattacks. The higher the number of devices, the greater the associated risk factor in manufacturing plants. Attacks on OT infrastructure have a high potential to impact human lives due to the nature of the manufacturing environment.
HCLTech's 360° SecureOT is not just a technology solution; it's a programmatic approach to OT/ICS security that works in connection with operational processes and people within the organization. It helps businesses to plan and deploy cybersecurity solutions with minimal downtime, ensuring successful adaptability through awareness programs. By leveraging our capabilities, global enterprises can genuinely secure their digital and converged IT/OT infrastructure in manufacturing organizations, ensuring safety and risk-free operations to drive digital innovation and supercharge their growth.






